Question #181
An application writes items to an Amazon DynamoDB table. As the application scales to thousands of instances, calls to the DynamoDB API generate occasional
ThrottlingException errors. The application is coded in a language incompatible with the AWS SDK.
How should the error be handled?
- A. Add exponential backoff to the application logic
- B. Use Amazon SQS as an API message bus
- C. Pass API calls through Amazon API Gateway
- D. Send the items to DynamoDB through Amazon Kinesis Data Firehose
Correct Answer: A
Reference:
https://docs.aws.amazon.com/amazondynamodb/latest/developerguide/Programming.Errors.html
Question #182
An application deployed on AWS Elastic Beanstalk experiences increased error rates during deployments of new application versions, resulting in service degradation for users. The Development team believes that this is because of the reduction in capacity during the deployment steps. The team would like to change the deployment policy configuration of the environment to an option that maintains full capacity during deployment while using the existing instances.
Which deployment policy will meet these requirements while using the existing instances?
- A. All at once
- B. Rolling
- C. Rolling with additional batch
- D. Immutable
Correct Answer: D
Reference:
https://aws.amazon.com/blogs/developer/version-2-of-the-aws-elastic-beanstalk-windows-server-platform/
Question #183
A Developer is working on an application that handles 10MB documents that contain highly-sensitive data. The application will use AWS KMS to perform client- side encryption.
What steps must be followed?
- A. Invoke the Encrypt API passing the plaintext data that must be encrypted, then reference the customer managed key ARN in the KeyId parameter
- B. Invoke the GenerateRandom API to get a data encryption key, then use the data encryption key to encrypt the data
- C. Invoke the GenerateDataKey API to retrieve the encrypted version of the data encryption key to encrypt the data
- D. Invoke the GenerateDataKey API to retrieve the plaintext version of the data encryption key to encrypt the data
Correct Answer: A
Question #184
A Developer is building a web application that uses Amazon API Gateway to expose an AWS Lambda function to process requests from clients. During testing, the Developer notices that the API Gateway times out even though the Lambda function finishes under the set time limit.
Which of the following API Gateway metrics in Amazon CloudWatch can help the Developer troubleshoot the issue? (Choose two.)
- A. CacheHitCount
- B. IntegrationLatency
- C. CacheMissCount
- D. Latency
- E. Count AD
Correct Answer: Explanation
Question #185
An AWS Lambda function must access an external site by using a regularly rotated user name and password. These items must be kept securely and cannot be stored in the function code.
What combination of AWS services can be used to accomplish this? (Choose two.)
- A. AWS Certificate Manager (ACM)
- B. AWS Systems Manager Parameter Store
- C. AWS Trusted Advisor
- D. AWS KMS
- E. Amazon GuardDuty
Correct Answer: BD
Question #186
A Developer is trying to deploy a serverless application using AWS CodeDeploy. The application was updated and needs to be redeployed.
What file does the Developer need to update to push that change through CodeDeploy?
- A. dockerrun.aws.json
- B. buildspec.yml
- C. appspec.yml
- D. ebextensions.config
Correct Answer: C
Question #187
A Developer wants to upload data to Amazon S3 and must encrypt the data in transit.
Which of the following solutions will accomplish this task? (Choose two.)
- A. Set up hardware VPN tunnels to a VPC and access S3 through a VPC endpoint
- B. Set up Client-Side Encryption with an AWS KMS-Managed Customer Master Key
- C. Set up Server-Side Encryption with AWS KMS-Managed Keys
- D. Transfer the data over an SSL connection
- E. Set up Server-Side Encryption with S3-Managed Keys
Correct Answer: BD
Question #188
A company is running a Docker application on Amazon ECS. The application must scale based on user load in the last 15 seconds.
How should a Developer instrument the code so that the requirement can be met?
- A. Create a high-resolution custom Amazon CloudWatch metric for user activity data, then publish data every 30 seconds
- B. Create a high-resolution custom Amazon CloudWatch metric for user activity data, then publish data every 5 seconds
- C. Create a standard-resolution custom Amazon CloudWatch metric for user activity data, then publish data every 30 seconds
- D. Create a standard-resolution custom Amazon CloudWatch metric for user activity data, then publish data every 5 seconds
Correct Answer: B
Question #189
A company needs to ingest terabytes of data each hour from thousands of sources that are delivered almost continually throughout the day. The volume of messages generated varies over the course of the day. Messages must be delivered in real time for fraud detection and live operational dashboards.
Which approach will meet these requirements?
- A. Send the messages to an Amazon SQS queue, then process the messages by using a fleet of Amazon EC2 instances
- B. Use the Amazon S3 API to write messages to an S3 bucket, then process the messages by using Amazon Redshift
- C. Use AWS Data Pipeline to automate the movement and transformation of data
- D. Use Amazon Kinesis Data Streams with Kinesis Client Library to ingest and deliver messages
Correct Answer: D
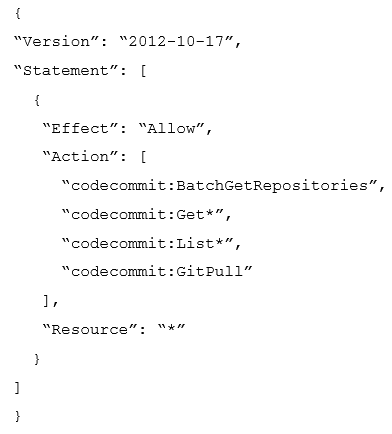
Question #190
A Developer accesses AWS CodeCommit over SSH. The SSH keys configured to access AWS CodeCommit are tied to a user with the following permissions:
The Developer needs to create/delete branches.
Which specific IAM permissions need to be added, based on the principle of least privilege?
- A. “codecommit:CreateBranch” “codecommit:DeleteBranch”
- B. “codecommit:Put*”
- C. “codecommit:Update*”
- D. “codecommit:*”
Correct Answer: C




Thank you !!
Helped me in achieving my aws developer certification.